Cyber Security
Our Cyber Security Solutions
Cyber Security Consulting
Our high-quality cybersecurity consultancy services will ensure that your business thrives in an environment of growing cyber crime.
Security Operations Centre
Monitor your organization’s entire IT infrastructure, 24/7, to detect and respond to cybersecurity events in real-time.
Vulnerability Assessment
Let’s evaluate security risks on your systems to reduce the probability for intruders to get unauthorized access of systems.
Penetration Testing
We will simulate a variety of attacks that could threaten your business. We examine whether a system is robust enough to withstand attacks.
Digital Forensics
After a security breach, we have the expertise to analyze the breach to determine how it happened and try to amass the evidence to prove who perpetrated the act.
Information Systems Security
Management Certification (ISO27001 Certification Attain the only auditable standard that deals with the overall management of information security, rather than just which technical controls to implement.
Cyber Threat Intelligence
We show your company the various risks you face from external threats, their capabilities and motivation, and the indicators of compromise (IOCs).
Security Incident and Event Management (SIEM Implementation)
Recognise potential security threats and vulnerabilities before they have a chance to disrupt business operations.
Improve Your Organization's Security Posture
Do you require an in-house or outsourced team of IT security professionals that monitors your organization’s entire IT infrastructure, 24/7, to detect cybersecurity events in real-time and address them as quickly and effectively as possible?
24/7 Monitoring & Response
Security Operations Centre
Having a SOC can improve customer confidence, simplify and strengthen your organization's compliance with industry, national and global privacy regulations. The SOC team implements the organization’s overall cybersecurity strategy and acts as the central point of collaboration in coordinated efforts to monitor, assess, and defend against cyberattacks.



Cyber Security Consulting
Industry-Relevant Threat Intelligence
The rise of cyber crime reiterates the importance of cyber security for businesses of all sizes and scales. Develop a strategy to fend off most attacks and recover quickly.
Vulnerability Assessment
Royal iTech evaluates security risks on your website, software, hardware systems and network to reduce the probability of threats. We examine whether a system is robust enough to withstand attacks from authenticated and unauthenticated positions, as well as a range of system roles.


ISO27001 Certification
Information Systems Security Management Certification is an internationally recognised specification for an Information Security Management System, or ISMS. It’s the only auditable standard that deals with the overall management of information security, rather than just which technical controls to implement. Our team can guide you to become ISO 27001 complaint. To achieve certification, we will assist your organization through a two step process .
Penetration Testing
Complete online security, on all of your devices
We look for ways to find and exploit any vulnerabilities you may have and work with you to help eliminate those vulnerabilities


Cyber Intelligence Gathering
Cyber threat intelligence (CTI), is information gathered from a range of sources about current or potential attacks against your organization. The information is analyzed, refined and organized and then used to minimize and mitigate cybersecurity risks. We provide security against digital threats such as hackers that aim to steal sensitive information over the Internet. We show your company the various risks you face from external threats, such as zero-day threats and advanced persistent threats (APTs).
Some of Our Clients






Digital Forensics
Stop data breach right in its tracks
Our team has built the capacity for preservation, identification, extraction, and documentation of computer evidence. We can find evidence from digital media like a computer, mobile phone, server, or network. Our forensic team work with the best techniques and tools to solve complicated digital-related cases.
Are you experiencing any of the following?
- Data Breach Incident
- Issues with Disgruntled Employees
- Intellectual Property Theft or Trade Secrets
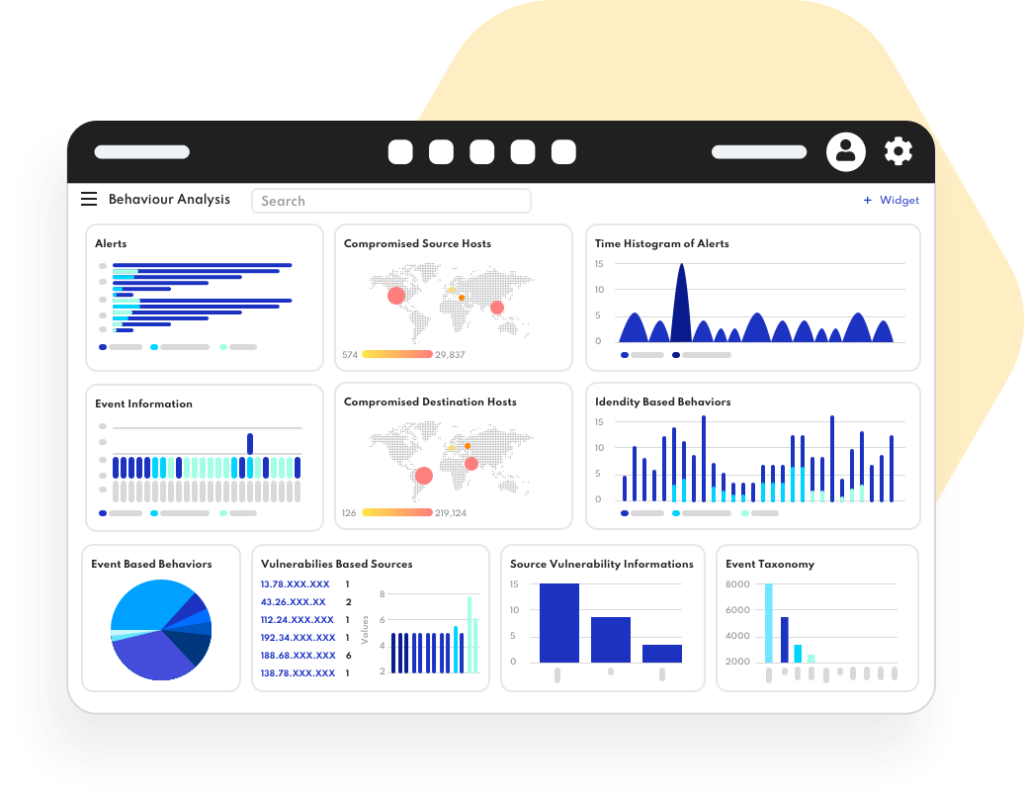
Security Incident and Event Management
The SIEM is a security solution that helps organizations recognize potential security threats and vulnerabilities before they have a chance to disrupt business operations. It surfaces user behavior anomalies and uses artificial intelligence to automate many of the manual processes associated with threat detection and incident. This solution perform some level of data aggregation, consolidation, and sorting functions in order to identify threats and adhere to data compliance requirements.






